Network Design and Architecture
Overview
Network design and architecture refer to the strategic process of planning and creating a network infrastructure to meet specific business, operational, or technical needs. It encompasses various elements such as hardware, software, topology, protocols, and security measures. Here's an overview:
Below is our approach for Network design and architecture for the organization's needs in terms of performance, scalability, security, and reliability. Here's our step-by-step approach to network and architecture design:
Our Methodology
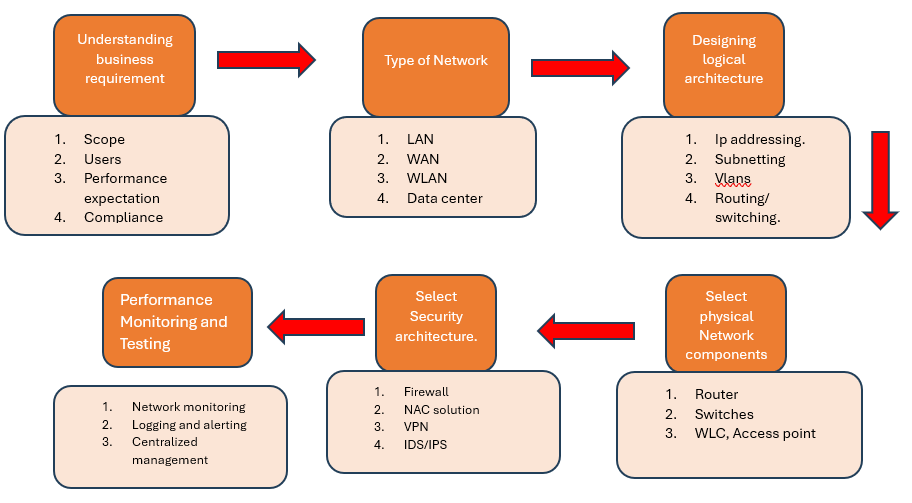
Understand Business Requirements
- Scope: What will the network be used for? (e.g., data transfer, video conferencing, online transactions)
- Users: How many users or devices will the network support?
- Performance Expectations: What is the latency, bandwidth, and reliability needs?
- Compliance: Are there any regulatory requirements (e.g., data privacy laws, security regulations)?
Determine the Type of Network
LAN (Local Area Network): Typically used for small areas such as office buildings or campuses.WAN (Wide Area Network): For larger geographical areas, connecting remote sites or offices.
WLAN (Wireless LAN): A wireless extension of a LAN.
Data Center Network: Highly optimized for supporting server-to-server and storage traffic.
Cloud Network: Integrating with cloud service providers for scalability and flexibility
Design Logical Network Architecture
- Subnetting: Break the network into smaller sub-networks (subnets) for easier management and security.
- IP Addressing Scheme: Define a structured and scalable IP addressing plan.
- VLANs (Virtual Local Area Networks): Use VLANs to logically separate network traffic based on departments or functions.
- Routing & Switching: Determine how data will flow between devices and subnets. Use routers and switches to manage traffic efficiently.
- Traffic Management: Implement policies like QoS (Quality of Service) to prioritize mission-critical traffic
Select Physical Components
- Core Switches and Routers: High-performance devices to handle the core network traffic.
- Edge Switches: Located closer to users, these handle local traffic before routing it to core devices.
- Wireless Access Points: For Wi-Fi coverage, choose APs that support the latest wireless standards (e.g., Wi-Fi 6).
- • Firewalls & Security Devices: Ensure that firewalls, intrusion detection/prevention systems (IDS/IPS), and other security appliances are in place.
- Servers and Storage: Plan the placement and redundancy of servers and storage systems.
- Cabling: Choose between fiber optics (for long distances and high-speed transmission) and copper cabling (for short-range communication).
Design Security Architecture
- Firewalls: Use firewalls at the network perimeter to control traffic entering or leaving the network.
- Encryption: Encrypt sensitive data, both at rest and in transit.
- Network Access Control (NAC): Implement NAC to ensure that only authorized devices can connect to the network.
- Segmentation: Use network segmentation to isolate sensitive data or systems from the broader network.
- Intrusion Detection and Prevention Systems (IDS/IPS): Implement systems to detect and prevent malicious activity.
- VPN (Virtual Private Network): For secure remote access.
Monitoring and Management
- Network Monitoring Tools: Use tools like SNMP-based monitoring systems to track performance, availability, and security in real-time.
- Logging and Alerting: Set up logging mechanisms and automated alerts to detect potential issues before they become critical.
- Centralized Management: If possible, use centralized management platforms to handle network devices, configurations, and security policies

